It seems like we hear about a new major network infiltration, data leak, or ransomware attack almost daily. But unlike the TV image, most hackers are not executing complex code or exploiting vulnerabilities in unpatched systems. On the contrary, the most easily exploited weakness in modern cyber infrastructure is the people who use it.
Hackers have found it is much easier to trick people than it is to trick computers. Their goal is to maximize the amount of profit they can make from tricking someone the least amount of times. It is for this reason that a Microsoft account makes a tantalizing target.
A Microsoft account is often tied to many different systems and by compromising a single password, a hacker can gain access to all of them. A complex and unique password can be a great assistance in preventing this, but if you tell a hacker your password then no amount of complexity will save you.
You wouldn’t provide your password intentionally, but a hacker’s greatest hope is that you won’t know they’ve stolen your password. Imagine you have received an email saying “Unusual activity has been detected on your Microsoft account. Sign in here to verify your recent activity or your account will be locked out.”
You quickly sign in and check this activity and already you have fallen into their trap. The link you clicked took you to what appeared to be Microsoft’s normal sign in page.
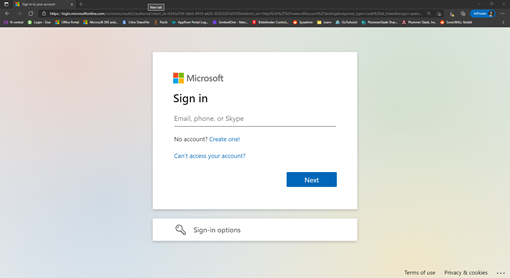
You signed in and seemed to connect as usual. But the page was fake. It was a tool the hacker used to play man in the middle between you and Microsoft’s server. Once you put in the password they pass along all legitimate information, leaving you none the wiser that your password has just been stolen.
How do we avoid this trap? After all, Microsoft can send email alerts about suspicious activity. How can we determine what emails are legitimate and which are fake?
The easiest way to win is not to play their game. Don’t click on a link in an email about your account. Always go directly to the website in your web browser instead of clicking the link. Portal.Microsoft.com will always take you to the correct website where you can sign in safely and review your account’s activity. Once signed in, you can click your initials at the top right and click “View Account”.
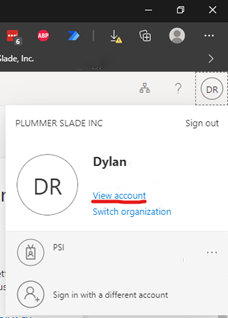
You can click “Review recent activity” to check your account activity.
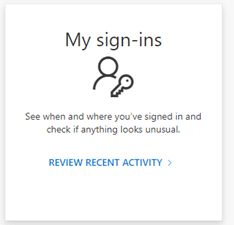
But what if you do get compromised? What if there is strange activity on your account? There are two immediate courses of action you should take.
- Let your IT know. Even if its just a quick email, your network team needs to know so they can start investigating and mitigating any possible security incidents.
- Change your password!
You can change your password from your profile:
If your Microsoft account is tied to your Active Directory account, you may need to change your password from your work computer instead of here. Use “Ctrl + Alt + Delete” while signed into your work computer to update the password. Your company’s server will update your Microsoft account within minutes. If you’re not sure which you should do, consult with your IT provider.